Introducing Diro: A Decentralized Identity & Access Management (dIAM)

WHAT IS DIRO?
The digital world today lack some credible identity system that is universally consumable and can be trusted by counter parties across industries. Also, all crowd sourcing based solutions lack credibility and verification hat is needed to address regulatory requirements. Getting all the industries, governments and consumers across hundreds of jurisdictions to agree on a framework has been a challenge.
The problem has been part technical and part political. Although, a great deal has already been written on challenges in creating universal identity
Owning identity itself is hard for individuals
Verifying real identities requires mass consensus and adoption
Centralized systems are unreliable in long term due security and political risks
DIRO is a Decentralized Identity and Access Application supported by crowdsourcing contact directory {for Network, Web, Application, IoT, Intelligent Contract, AR / VR, and all other domains using people resources.

Diro uses the power of the crowd’s intelligence to automatically tag people to the phone book for everyone.
These efforts continue to crash up to 50%, 66%, 75% and so on when people join the phone book.
These efforts continue to crash up to 50%, 66%, 75% and so on when people join the phone book.
Diro is a super productivity tool for implementing any Team size phone book for all members to view & manage. And you can also create a Contact List of clients or vendors and share with certain people.
Automated, organized and always up to date contacts with one click access to the service.
Make your contacts go live — be it the choice of IVR, wait times, last appointment or just miles or preferences with universalfrictionless access from within your contacts.
Crowd-resources directory contact
Reduced more than 90% of effort in managing contacts
Diro-using the power of crowd intelligence to automatically tag the person to phone book for everyone.
Efforts continue to reduce by 50%, 66%, 75% and beyond as people join the phone book.
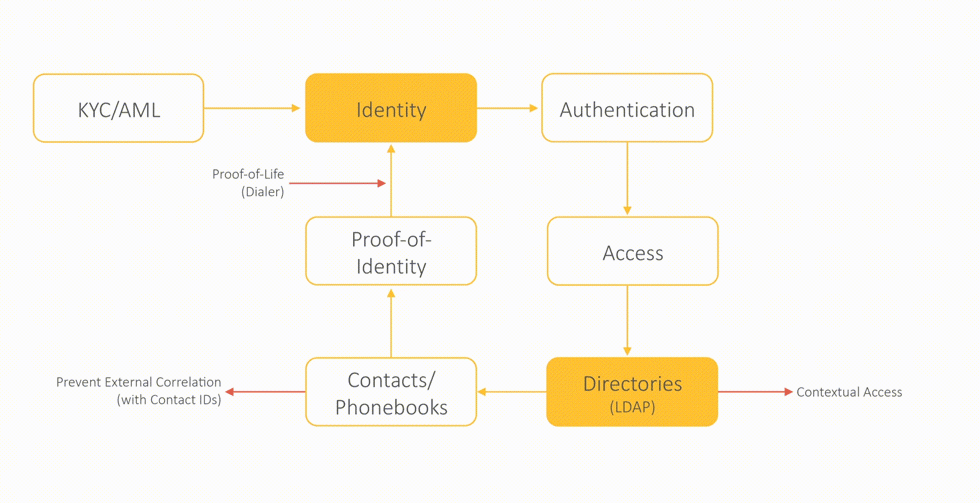
Proof-of-life to secure digital identity
With a Live conversation with friends and family.
Create Your identity of Sybil stand the whole group livehuman in verification and devices when you talk with your family and friends.
Never lose your private key and recover lost keys with confidence using fractional keys that are stored in the phone
Proof-of-Life to secure digital Identities
With Live conversations with friends and family.
Make your Identity Sybil resistant with livehuman verification across groups and devices when you speak to your family and friends.
Never loose your private key and recover lost keys with confidence using shards of the key stored on other phones
Decentralized IAM (dIAM) Market ($32bn Market by 2022)
Currently, IAM is highly fragmented & identities exist in silos of various service providers. The need for cyber security and access controls is growing at a compounding rate. Further, billions of IoT devices can not be controlled by a centralized identity provider, since a breach of this provider would prove catastrophic.
Directory Operating System
Crowd-automated contact management where:
Auto-organize contacts
Get missing contacts automatically
Auto updated contacts
Converged directory services
Experience shared contact directories with integrated access management using LDAP. Integrates multiple silos of identities across 1000s of platforms with simple contact app.
Password-less IAM
Eliminate need for hardware tokens or keys with open standards like Federated SSO with SAML, OAuth 2.0, OpenID Connect etc. With applications across multiple domains.
Universal Identities
Self Soverign Identities with seamless Global Pgp and digital signing infrastructure using SPKI and Self-service key retrieval (DPKI)
Eliminate synthetic identities
With the worlds largest passive social graph with SPKI. Further make identities Sybil resistant with Proof-of-life. Use patent pending cryptographic KYC for eliminating Identity fraud.
Automated privacy
Discover and use profile cards to automate privacy across the identity eco-system. Prevent external correlation using contact IDs. Unlock private contextual data from within contacts with cryptography and IAM frictionlessly.
Strong network effect
Creates large scale value through crowd mining and viral stacking. With top Identity use cases and being default dialer app diro maps the entire identity network with just 1% users.
FOR MORE INFORMATION ABOUT THE DECENTRALIZED IDENTITY AND ACCESS MANAGEMENT (dIAM), PLEASE VISIT THE FOLLOWING:
Website: http://www.diro.io/
Announcement Thread : https://bitcointalk.org/index.php?topic=3266144.msg34032664#msg34032664
Facebook : https://www.facebook.com/DiroBlockchain
Twitter : https://twitter.com/DiroLabs
Bitcointalk profile: https://bitcointalk.org/index.php?action=profile;u=1671465
ETH address: 0xAd1043Acec7feED090458C1Fe7667a2014a13FA6

Komentar
Posting Komentar